It is no secret to the world that video is the most highly regarded part of the whole digital ecosystem, which every organization will strive to achieve, due to which content creators are always on the lookout for ways to secure video content. Videos are used for advertising, training, or delivering information.
In addition, delivery strategies for live and on-demand video content in the presence of security arrangements on video streaming platforms have been developed as very efficient strategies. On social media platforms, online videos, too, are very much prone to the harmful effects of content theft caused by hacking and piracy, just like any other digital property.
In this Article:
Hence, security and encryption are a must for an application that engages in streaming videos, which entails sensitive or personal information.
Hence, you must always ask yourself questions if you know what is right for you. Are you confident that your company is securely encrypted? What are you using your social media to do if you don’t go on manually to understand what is happening on it?
For the investigation, you would need to make sure that your capital is safe from a loss within your premises themselves, like the staff or the authorized zones. Is your company equipped with the necessary security rules and regulations?
Whether you are an avid hiker, a casual stroller, or somebody who just likes to be in nature, being away from the environment you love can weigh on your conscience and make you feel uneasy at times. As a business owner, you consult the spots on the general market not only to avoid the risk but to gain more audience.
Moreover, it is crucially important to understand the role of safe video streaming when using content and to take steps against video digital piracy; as more and more digital products are being made freely available online, there is a need to build a secure video environment.
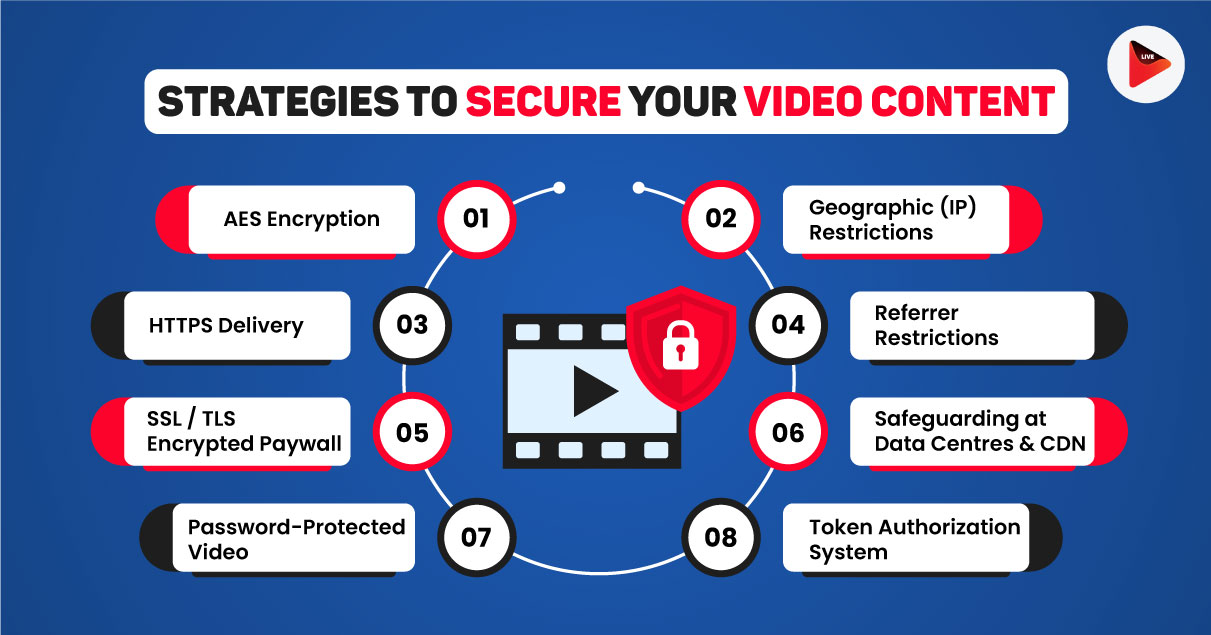
8 Strategies to Secure Video Content
Let’s explore in detail these security features placed around you to help you use standard protocols in your principal transmissions. Of the higher types protection of several of them occur by way of additional items such as incorporation.
1. AES Encryption:
Starting our talk on safe video streaming with an introduction of AES encryption is our main hedge. The acronym “AES” (Advanced Encryption Standard) is an encoding method that is unsure of common data security.
Only authorized personnel, in this case, can access your information. The Tech Target describes AES as a symmetric block cipher that the US government has utilized for secret data encrypting.
The most popular protocol is symmetric key encryption, which can be implemented in hardware and software platforms and is usually used to encrypt sensitive data worldwide. In brief, AES encryption helps speed up the process of protecting your stuff. The AES protocol processes data in ciphertext form to encrypt each stream using unique cryptographic keys.
Shannon Coventry, Marketing Manager at First Vehicle Leasing asserts, “To attain the information, guests are needed to have the essential digital key using the access location. There are options for users to peruse content on stream that has been authenticated, or for them to log in to view the things available. In other words, viewers will not be able to watch the video without the key because it will be depicted as an unorderly, intermittent, and random event without harmony between the aural and visual components.”
2. HTTPS Delivery:
The most distinguishing advantage of HTTPS is that it ensures that no third-party attacks can interfere with confidentiality. Coming to the example, many times, it is observed to occur along with video streaming that mainly a user has obtained the information from public networks such as libraries, educational institutions, etc.
These shots often come from cameras set in public premises, eavesdropping apps, and electronic snoops. Hackers jump at such unprotected networks to steal the data displayed directly to the viewer from these open networks.
“Different types of payload attacks are carried out using HTTPS, where the connection is encrypted on the website accessible to the user with the function of a digital certificate and encryption key,” says our expert, Lisa Ockinga, Chief Product Officer at First Vehicle Leasing
A unique HTTPS standard safeguards against eavesdropping on every transmission made to the movie viewer by tightly encrypting all of the data under a layer of security between the server and the transmitter. Thus, they guarantee that your work will be redundant and have greater protection against any form of plagiarism.
I will explain HTTPS protocol distribution to the audience, an extraordinary online video security measure that can be quickly adopted.
3. SSL / TLS Encrypted Paywall:3. SSL / TLS Encrypted Paywall:
Transit Layer Security (TLS) and Secure Socket Layer (SSL) are standard security systems that encrypt data flow between a client and a remote server. They use this kind of encryption based on cryptographic algorithms, which are also meant to protect your financial information.
The technique may include safeguarding private and sensitive data, probably in both situations. This is especially true when consumers open a site such as that with a video paywall.
Therefore, when using OTT video to monetize content, encrypting the data with SSL/TLS is essential to avoid offending or harming users. Specifically, a VPN ensures the safety of any data transmitted on the Internet.
This helps to give a personal feel to the services provided by servers and customers, therefore serving to establish a relationship between them.
The paywalls should, in a sense, provide the chance to earn the necessary cash for the kind of content and the payment in a diversity of currencies, including credit and debit cards. Indeed, the most meaningful thing to remember is to ensure the viewers’ safety while your streaming platform is accessed through a secure network.
4. Password-Protected Video:
“The password wallet should be used whenever you would like to publicly watch screencasts with people. This is a perfect technique to avoid having illegitimate users who would hurt the status of your resource. Nevertheless, the fact remains that same—passwords, as is known to everyone, are the least secure solution since they are likely to be exposed to hacker attacks or leaks,” says Mark McShane, Director of Link Building at Help a Reporter Out (HARO)
Remember that as you consider this alternative, you should never forget that certain risks can be attributed to this action. Meanwhile, the primary security measure to delimit an attack by this means has been the implementation of passwords.
First, the encryption of the video that you want to distribute is necessary. The easiest way to defend assets may look like restricting the wrongly conceited people from having access, but the more important strategy is this.
To add, the users must enter the correct password to get into the videos. By this, it can be inferred that as long as they are not succeeding in passing the password, it does not match.
5. Geographic (IP) Restrictions:
According to Windy Ko, HARO links specialist at Cupid PR, “Through the practice of IP or regional restrictions, you’ll ensure the world’s most precious contents are adequately protected, thereby shielding this precious information from people in other regions. You must be aware that people who could see your content (legit visitors) can be prevented due to the nature of bots. Whenever some regions are considered more likely to have a higher chance of piracy, the other places are less known to be a threat. Statistical information demonstrates that the country’s Office of the trade representative holds over thirty countries as areas of potential infection. In addition, geoblocking remains in many cases. IP regulations may be one of the many aspects that you may need to consider depending on where your audiences are from. Geo-fencing, a surrounding portion of video streaming services, is a security tool that alleviates piracy.”
Most film companies today are specifically designing their films for people in one or a few of the world’s nations. To illustrate, “geo-blocks” in designated conditions become convenient to suspend only those specific locations and at the same time blacklist the entire others.
6. Referrer Restrictions:
“Presently, the safety logic is effective, though; there is more of an environment that can be created where safety is not only a buzzword but used to exploit the potential of secure video streaming. In addition, stipulating the number of views to be attributed to your videos as a defensive approach will be of the essence. This is how they operate – throughout your website and any other affiliate site you might have access to, they add them to their whitelist of domain lists. The opposite is true for this function, as it is a protected network of digital financial tokens normally coordinated by the control server. As a result, it can interrupt the airflow of any multimedia video found on a pirate page. Attempting to embed a video of your choice, which has been chosen with such great care everywhere, is impossible,” says Holly Cooper, Marketing Manager at Windows & Doors UK.
7. Safeguard Your Content at Data Centres & CDN:
“You market content using vast networks of content delivery networks (CDN) and data centers with delivery-level security guarantees. This product can be integrated into an online video platform. A content delivery network (CDN) is a computer network that ensures the prompt and secured distribution of content and streaming data by installing sophisticated load-balancing software. Hosting through a combined CDN online video platform is one way of retrieving your assets from various threats. DDoS attacks, which compromise an attacker to disrupt the service being sought by sending massive traffic, are major deficits. The use of CDN here makes it impossible to launch such a cyber attack. More than that, these frameworks implement things such as redundancy, which will eliminate all low content risks and accelerate the loading speeds,” says Adam Crossling, Marketing & New Business Director at zenzero
8. Token Authorization System:
“There is a system in place that uses a tokenization approach which was not available previously to disseminate videos securely over the Internet. The saying here implies that those coins are significant parts of the story which can be used as evidence that allows whoever is taking the stream to be confirmed. As users who are entitled to watch online videos begin doing so, the tokenizing system used by the video platform not only detects all the video streams but also ensures that the users are allowed to do so. This feature uses tokens to operate that act as a safeguard against illicit items that may be present on your exclusive online video hub. The video players can be enabled to simultaneously send requests for fresh tokens from the server every two minutes where dynamic tokenized video security has been enabled as an option,” says Sasha Quail, Business Development Manager of claims.co.uk
In summary:
We’ve finally come to the end of the discussion regarding the most suitable resources and methods to secure video content. In addition, you should be aware of the security and safety measures to be considered for preventing the hassles in your online videos.
Let me cite something more practical, for instance, the search engine of movies, where GIFs and pictures of movie stars have been created. A third type is those who choose the integrated video feature and simply add plug-ins to the existing software.
Countless companies barely wait for rails to which they can hang their hats. They do not take safety into account. Finally, they do not even care whether they are top value. Ascend through the gateway to a favored future of security, sparing the hassle of money worries invested endlessly anytime.
OneStream Live is a cloud-based live streaming solution to create, schedule, and multistream professional-looking live streams across 45+ social media platforms and the web simultaneously. For content-related queries and feedback, write to us at [email protected]. You’re also welcome to Write for Us!